ssllabs SSL Server Tester
What is ssllabs SSL Server Tester?
✍: FYIcenter.com
![]() ssllabs SSL Server Tester
is an online tool that checks a specified Website
to see if its SSL/TLS certificate is installed correctly or not.
ssllabs SSL Server Tester
is an online tool that checks a specified Website
to see if its SSL/TLS certificate is installed correctly or not.
Here is the description provided by sslshopper: "This free online service performs a deep analysis of the configuration of any SSL web server on the public Internet."
You can follow these steps to try ssllabs SSL Server Tester:
1. Go to https://www.ssllabs.com/ssltest/.
2. Enter the URL of the Website you want to check, for example, www.visa.com.
3. Click "Submit" button. You will see the output of the test:
SSL Report: www.visa.com (23.56.121.100):
Summary
Overall Rating: A
Certificate: 100
Protocol Support: 95
Key Exchange: 90
Cipher Strength: 90
Authentication:
Server Key and Certificate #1
Subject - www.visa.com
Fingerprint SHA1: 0e7c6e5f89eee96f1721ac192916709a699010b2
Pin SHA256: CsAs3jSOlThqXOphLtPAMENTNbe5UONPcA8Hie+8t+A=
Common names - www.visa.com
Alternative names - promocoesvisa.com.br www.visa.ca visa.com ...
Valid from - Fri, 27 May 2016 00:00:00 UTC
Valid until - Sat, 26 Aug 2017 23:59:59 UTC (expires in 1 year and 1 month)
Key - RSA 2048 bits (e 65537)
Weak key (Debian) - No
Issuer - GeoTrust SSL CA - G3
AIA: http://gn.symcb.com/gn.crt
Signature algorithm - SHA256withRSA
Extended Validation - No
Certificate Transparency - Yes (certificate)
Revocation information - CRL, OCSP
CRL: http://gn.symcb.com/gn.crl
OCSP: http://gn.symcd.com
Revocation status - Good (not revoked)
Trusted - Yes
Additional Certificates (if supplied)
Certificates provided - 2 (3403 bytes)
Chain issues - None
#2
Subject - GeoTrust SSL CA - G3
Fingerprint SHA1: 5aeaee3f7f2a9449cebafeec68fdd184f20124a7
Pin SHA256: PbNCVpVasMJxps3IqFfLTRKkVnRCLrTlZVc5kspqlkw=
Valid until - Fri, 20 May 2022 21:36:50 UTC (expires in 5 years and 10 months)
Key - RSA 2048 bits (e 65537)
Issuer - GeoTrust Global CA
Signature algorithm - SHA256withRSA
Certification Paths
Path #1: Trusted
1 - Sent by server - www.visa.com
Fingerprint SHA1: 0e7c6e5f89eee96f1721ac192916709a699010b2
Pin SHA256: CsAs3jSOlThqXOphLtPAMENTNbe5UONPcA8Hie+8t+A=
RSA 2048 bits (e 65537) / SHA256withRSA
2 - Sent by server - GeoTrust SSL CA - G3
Fingerprint SHA1: 5aeaee3f7f2a9449cebafeec68fdd184f20124a7
Pin SHA256: PbNCVpVasMJxps3IqFfLTRKkVnRCLrTlZVc5kspqlkw=
RSA 2048 bits (e 65537) / SHA256withRSA
3 - In trust store - GeoTrust Global CA Self-signed
Fingerprint SHA1: de28f4a4ffe5b92fa3c503d1a349a7f9962a8212
Pin SHA256: h6801m+z8v3zbgkRHpq6L29Esgfzhj89C1SyUCOQmqU=
RSA 2048 bits (e 65537) / SHA1withRSA
Weak or insecure signature, but no impact on root certificate
Configuration:
Protocols
TLS 1.2 - Yes
TLS 1.1 - Yes
TLS 1.0 - Yes
SSL 3 - No
SSL 2 No
Cipher Suites (SSL 3+ suites in server-preferred order; deprecated and SSL 2 suites at the end)
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) ECDH secp256r1 (eq. 3072 bits RSA) FS - 256
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) ECDH secp256r1 (eq. 3072 bits RSA) FS - 128
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) ECDH secp256r1 (eq. 3072 bits RSA) FS - 256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) ECDH secp256r1 (eq. 3072 bits RSA) FS - 256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027) ECDH secp256r1 (eq. 3072 bits RSA) FS - 128
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) ECDH secp256r1 (eq. 3072 bits RSA) FS - 128
TLS_RSA_WITH_AES_256_GCM_SHA384 (0x9d) - 256
TLS_RSA_WITH_AES_128_GCM_SHA256 (0x9c) - 128
TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d) - 256
TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) - 128
TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) - 128
TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) - 112
Handshake Simulation
Android 2.3.7 No SNI 2 - RSA 2048 (SHA256) - TLS 1.0 - TLS_RSA_WITH_AES_128_CBC_SHA No FS
Android 4.0.4 - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Android 4.1.1 - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Android 4.2.2 - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Android 4.3 - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Android 4.4.2 - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Android 5.0.0 - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Android 6.0 - RSA 2048 (SHA256) - TLS 1.2 > http/1.1 - TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Baidu Jan 2015 - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
BingPreview Jan 2015 - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Chrome 51 / Win 7 R - RSA 2048 (SHA256) - TLS 1.2 > h2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Firefox 31.3.0 ESR / Win 7 - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Firefox 45 / Win 7 R - RSA 2048 (SHA256) - TLS 1.2 > h2 - TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Firefox 46 / Win 7 R - RSA 2048 (SHA256) - TLS 1.2 > h2 - TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Googlebot Feb 2015 - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
IE 6 / XP No FS 1 No SNI 2 - Server closed connection
IE 7 / Vista - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
IE 8 / XP No FS 1 No SNI 2 - RSA 2048 (SHA256) - TLS 1.0 - TLS_RSA_WITH_3DES_EDE_CBC_SHA
IE 8-10 / Win 7 R - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
IE 11 / Win 7 R - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
IE 11 / Win 8.1 R - RSA 2048 (SHA256) - TLS 1.2 > http/1.1 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
IE 10 / Win Phone 8.0 - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
IE 11 / Win Phone 8.1 R - RSA 2048 (SHA256) - TLS 1.2 > http/1.1 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
IE 11 / Win Phone 8.1 Update R - RSA 2048 (SHA256) - TLS 1.2 > http/1.1 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
IE 11 / Win 10 R - RSA 2048 (SHA256) - TLS 1.2 > h2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Edge 13 / Win 10 R - RSA 2048 (SHA256) - TLS 1.2 > h2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Edge 13 / Win Phone 10 R - RSA 2048 (SHA256) - TLS 1.2 > h2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Java 6u45 No SNI 2 - RSA 2048 (SHA256) - TLS 1.0 - TLS_RSA_WITH_AES_128_CBC_SHA No FS
Java 7u25 - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA ECDH secp256r1 FS
Java 8u31 - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
OpenSSL 0.9.8y - RSA 2048 (SHA256) - TLS 1.0 - TLS_RSA_WITH_AES_128_CBC_SHA No FS
OpenSSL 1.0.1l R - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
OpenSSL 1.0.2e R - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Safari 5.1.9 / OS X 10.6.8 - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Safari 6 / iOS 6.0.1 R - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 6.0.4 / OS X 10.8.4 R - RSA 2048 (SHA256) - TLS 1.0 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Safari 7 / iOS 7.1 R - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 7 / OS X 10.9 R - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 8 / iOS 8.4 R - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 8 / OS X 10.10 R - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 9 / iOS 9 R - RSA 2048 (SHA256) - TLS 1.2 > h2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Safari 9 / OS X 10.11 R - RSA 2048 (SHA256) - TLS 1.2 > h2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Apple ATS 9 / iOS 9 R - RSA 2048 (SHA256) - TLS 1.2 > h2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Yahoo Slurp Jan 2015 - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
YandexBot Jan 2015 - RSA 2048 (SHA256) - TLS 1.2 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
DROWN (experimental) - No, server keys and hostname not seen elsewhere with SSLv2
Secure Renegotiation - Supported
Secure Client-Initiated Renegotiation - Yes
Insecure Client-Initiated Renegotiation - No
BEAST attack - Not mitigated server-side (more info) TLS 1.0: 0xc014
POODLE (SSLv3) - No, SSL 3 not supported (more info)
POODLE (TLS) - No (more info)
Downgrade attack prevention - Yes, TLS_FALLBACK_SCSV supported (more info)
SSL/TLS compression - No
RC4 - No
Heartbeat (extension) - No
Heartbleed (vulnerability) - No (more info)
OpenSSL CCS vuln. (CVE-2014-0224) - No (more info)
OpenSSL Padding Oracle vuln.
(CVE-2016-2107) - No (more info)
Forward Secrecy - With modern browsers (more info)
ALPN - Yes
NPN - Yes http/1.1 http/1.0
Session resumption (caching) - Yes
Session resumption (tickets) - Yes
OCSP stapling - No
Strict Transport Security (HSTS) - No
HSTS Preloading - Not in: Chrome Edge Firefox IE Tor
Public Key Pinning (HPKP) - No
Public Key Pinning Report-Only - No
Long handshake intolerance - No
TLS extension intolerance - No
TLS version intolerance - No
Incorrect SNI alerts - No
Uses common DH primes - No, DHE suites not supported
DH public server param (Ys) reuse - No, DHE suites not supported
SSL 2 handshake compatibility - Yes
Miscellaneous
Test date - Sun, 17 Jul 2016 02:03:33 UTC
Test duration - 63.903 seconds
HTTP status code - 301
HTTP forwarding - http://usa.visa.com PLAINTEXT
HTTP server signature - AkamaiGHost
Server hostname - a23-56-121-100.deploy.static.akamaitechnologies.com
The picture below shows you ssllabs SSL Server Tester output on www.visa.com:
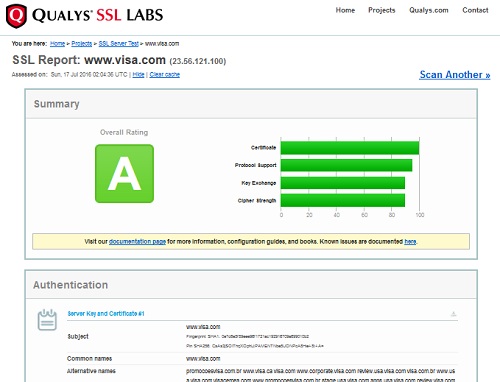
⇒ ssllabs SSL Server Tester Failed Example
⇐ High-Tech Bridge Free SSL Server Tester Failed Example
2016-10-08, ∼4816🔥, 0💬