*.berkeley.edu, Comodo PremiumSSL Wildcard, IST-IS, Universit...
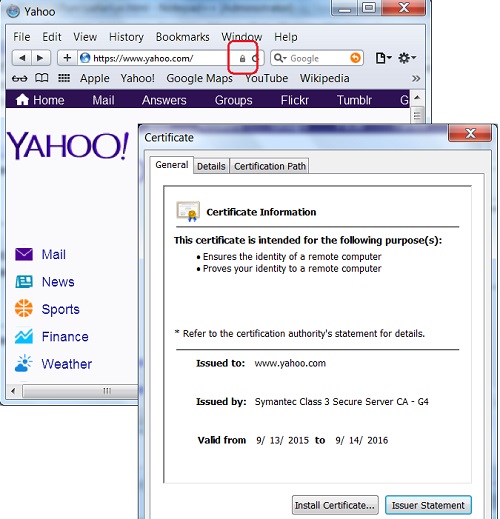
Certificate summary -
Owner: *.berkeley.edu, Comodo PremiumSSL Wildcard, IST-IS, University of California at Berkeley, STREET="200 California Hall #1500", L=Berkeley, ST=California, OID.2.5.4.17=947201500, US
Issuer: InCommon Server CA, InCommon, Internet2, US
Expiration: Mon Apr 14 19:59:59 EDT 2014
MD5: 33:DB:FA:22:8A:A8:69:44:E7:49:E9:64:53:AD:33:C0
Hash: Owner Hash=8a17b14e, Issuer Hash=84df5188
✍: FYIcenter.com
Information extracted out of the certificate:
Owner: CN=*.berkeley.edu, OU=Comodo PremiumSSL Wildcard, OU=IST-IS,
O=University of California at Berkeley, STREET="200 California Hall #1500",
L=Berkeley, ST=California, OID.2.5.4.17=947201500, C=US
Issuer: CN=InCommon Server CA, OU=InCommon, O=Internet2, C=US
Serial number: f8b4e9ac6ed6003097d154c24bb254
Valid from: Thu Apr 14 20:00:00 EDT 2011 until: Mon Apr 14 19:59:59 EDT
2014
Certificate fingerprints:
MD5: 33:DB:FA:22:8A:A8:69:44:E7:49:E9:64:53:AD:33:C0
SHA1: 49:BC:EE:03:01:0B:AD:2C:5B:A6:2F:D2:71:43:81:49:B7:2E:C0:71
SHA256:
EE:3A:0C:E7:FB:49:E4:C3:5A:EE:2C:E8:46:01:92:00:DE:D2:20:FF:46:22:15:A1:7B:
AF:8C:23:65:CE:58:B1
Signature algorithm name: SHA1withRSA
Version: 3
Extensions:
#1: ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: caIssuers
accessLocation: URIName: http://cert.incommon.org/InCommonServerCA.crt
,
accessMethod: ocsp
accessLocation: URIName: http://ocsp.incommon.org
]
]
#2: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 48 4F 5A FA 2F 4A 9A 5E E0 50 F3 6B 7B 55 A5 DE HOZ./J.^.P.k.U..
0010: F5 BE 34 5D ..4]
]
]
#3: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:false
PathLen: undefined
]
#4: ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://crl.incommon.org/InCommonServerCA.crl]
]]
#5: ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [1.3.6.1.4.1.5923.1.4.3.1.1]
[PolicyQualifierInfo: [
qualifierID: 1.3.6.1.5.5.7.2.1
qualifier: 0000: 16 34 68 74 74 70 73 3A 2F 2F 77 77 77 2E 69 6E
.4https://www.in
0010: 63 6F 6D 6D 6F 6E 2E 6F 72 67 2F 63 65 72 74 2F common.org/cert/
0020: 72 65 70 6F 73 69 74 6F 72 79 2F 63 70 73 5F 73 repository/cps_s
0030: 73 6C 2E 70 64 66 sl.pdf
]] ]
]
#6: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
#7: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_Encipherment
]
#8: ObjectId: 2.5.29.17 Criticality=false
SubjectAlternativeName [
DNSName: *.berkeley.edu
]
#9: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: AF 00 81 A1 E7 28 20 7F 0D AE 7C AD 0B 4E 25 0E .....( ......N%.
0010: 72 A5 13 E3 r...
]
]
Certificate in PEM format (Base64 encoded X.509):
-----BEGIN CERTIFICATE----- MIIFdDCCBFygAwIBAgIQAPi06axu1gAwl9FUwkuyVDANBgkqhkiG9w0BAQUFADBR MQswCQYDVQQGEwJVUzESMBAGA1UEChMJSW50ZXJuZXQyMREwDwYDVQQLEwhJbkNv bW1vbjEbMBkGA1UEAxMSSW5Db21tb24gU2VydmVyIENBMB4XDTExMDQxNTAwMDAw MFoXDTE0MDQxNDIzNTk1OVowgesxCzAJBgNVBAYTAlVTMRIwEAYDVQQREwk5NDcy MDE1MDAxEzARBgNVBAgTCkNhbGlmb3JuaWExETAPBgNVBAcTCEJlcmtlbGV5MSIw IAYDVQQJFBkyMDAgQ2FsaWZvcm5pYSBIYWxsICMxNTAwMS0wKwYDVQQKEyRVbml2 ZXJzaXR5IG9mIENhbGlmb3JuaWEgYXQgQmVya2VsZXkxDzANBgNVBAsTBklTVC1J UzEjMCEGA1UECxMaQ29tb2RvIFByZW1pdW1TU0wgV2lsZGNhcmQxFzAVBgNVBAMU DiouYmVya2VsZXkuZWR1MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA 5+CA/eDYMcudR0xNBPrNLy0HjsiE6P5RN3dZZK+YCRP5efCGEGhjzTjKJhfKQ+3c Ok2Xm6q7kivlgzU8mHkTD2sRTpQrQ/vfj3QfCAHCBZfgixrs4enAAE0aCi9AJgcg bVMizgarDy6OA3prBCohBD6G+6dny+xtZavOJYldtZ6Xg7WRm/5Km2AotkxrxAMm wlvWjZOG4laXbUn0k8fjY6CrGytVA59zXlCs+PowATrat3BHrWHcn+1fp44UzAUN ZSIlz4cr7PK3IAQjvrjYSLa1AI3Fljhd4YA4ziVwlI8o86cB6ff1CP13tyuqflds oobr5bxKBw5hW/aNy9HfkwIDAQABo4IBqzCCAacwHwYDVR0jBBgwFoAUSE9a+i9K ml7gUPNre1Wl3vW+NF0wHQYDVR0OBBYEFK8AgaHnKCB/Da58rQtOJQ5ypRPjMA4G A1UdDwEB/wQEAwIFoDAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMB BggrBgEFBQcDAjBdBgNVHSAEVjBUMFIGDCsGAQQBriMBBAMBATBCMEAGCCsGAQUF BwIBFjRodHRwczovL3d3dy5pbmNvbW1vbi5vcmcvY2VydC9yZXBvc2l0b3J5L2Nw c19zc2wucGRmMD0GA1UdHwQ2MDQwMqAwoC6GLGh0dHA6Ly9jcmwuaW5jb21tb24u b3JnL0luQ29tbW9uU2VydmVyQ0EuY3JsMG8GCCsGAQUFBwEBBGMwYTA5BggrBgEF BQcwAoYtaHR0cDovL2NlcnQuaW5jb21tb24ub3JnL0luQ29tbW9uU2VydmVyQ0Eu Y3J0MCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5pbmNvbW1vbi5vcmcwGQYDVR0R BBIwEIIOKi5iZXJrZWxleS5lZHUwDQYJKoZIhvcNAQEFBQADggEBAFm2/yFKO2TB +6CjEgWLfJoerM3jD+8AEFgmVQSzZoNIOwf+L1mle8u7Iyzi4Wrg4/ShTN+9l7rw rKwG/87gasG2X+SvfvUe5sUfjGdglcaoT2ENx6wkYNhSIK3RBCJMEX1CpPlA7i6p 8bStWrD6UdJ0g/PvjJzN/5xdRCf9NvMhjnG93hJrwS9LLoTFuk6uzZtGf5QZWW+x 3PFOJSyBOKj6NmmRGKJEBYK22PUGtWiPa3qRohdukFHO/mjAndqWlaSQ+zJwmdnf +mYMOPMOQPAq8Oi29T9D4PG7FTwsJhEjeAbPYv6bnIn0CdN3LFDtR4US5vrKYOWE OEtDyi+GPKo= -----END CERTIFICATE-----
Visit the Web site using this certificate: https://www.berkeley.edu
2015-07-16, ∼2545🔥, 0💬